Log in online: LIMIT is easy to use and packed with useful features.
Simply put, Profile Officers carry out their rounds, reporting in with location and event data. Their Supervisors, Managers and now you, the client, can interact like never before using the LIMIT dashboard, accessible online via your PC.
LIMIT in more detail
LIMIT is a Unix-based platform that operates on the client’s premises.
Like many Patrol Management Systems, it uses Near Field Communication (NFC) short-range wireless technology to collect data from tags placed at strategic points around your site. But LIMIT can do much more than conventional systems:
Officers complete a report under a pre-determined list of headings:
- Accident Report Forms
- Reporting Accidents on site
- Incident Report Statement
- Actual Security Incidents
- Facilities Report Statement
- Any Building or property faults
- Health and Safety Report Statement
- H & S Incidents / Faults
- Visitor Sign In
- Water Run Off Forms
- Site Specific Reports
Images from the scene can be attached before signing and submitting each report.
These reports can be used in a court of law if required.
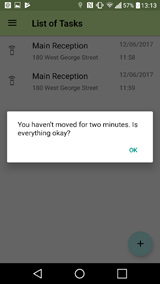
There is a built-in ‘officer down’ function that activates if the officer’s device is left horizontal for two minutes and hasn’t moved. If the officer does not respond, appropriate action is taken by our National Control Centre to ensure their welfare and safety.
At the end of their shift, Officers log out after completing any outstanding reports, responding to queries, or recording any missed patrol points so that Profile can report to the client with the reasons why.
There are different user roles in the system, each with its own permissions and access levels:
- Director
- Regional Manager
- Administrator
- Customer Service Manager
- Security Officer
- Mobile Manager
- Customer
Clients can select any available site from their personalised menu to view its stats individually.
Sites no longer under contract can be archived so that records can be reviewed later.
Region stats display events reported by the Officers and Mobile Managers.
Users can view events reported over specified periods of their choosing.
A Stats tab displays information about reports logged by Security Officers and Mobile Managers.
A Log Book tab shows detailed information about reported events with a breakdown by date and event types. Users can click on an event which will open a more detailed report in a separate tab.
A Map tab displays all tags and their positions on the site. Users can zoom in and out to view where tags are located and download a picture of a map.

Flexible, informative, controllable
Where LIMIT comes into its own to give Profile a distinct competitive advantage is how it puts the collected data and system features to work. Clients and their Customer Service Managers are able to manage many aspects of the system. They can:
- View a list of tags associated with a site, e.g. main door, exit #1, etc.
- View and edit specific tag information, and set up regular or recurring tasks.
- View a list of devices associated with a site.
- View different regions associated with their contracts and create new regions.
- View a list of employees and customers who have access to the website, or Security Officers and Mobile Managers with access to the LIMIT system.
- Draw a patrol area for a site so that when Security Officers wander outside of the drawn area, they get notified.
- Write a list of tasks that need to be performed on a daily basis.
- Compile site stats to compare actual performance by Security Officers to planned performance each month. If actual stats do not match a planned performance, an exception report is created.
- Set up as many as three daily patrol shifts, then monitor and adjust them.
- Generate invoices that are linked to specific events, then send to the client and the account manager.
- Set up different event types so as to generate email notifications to selected personnel, be it their supervisors, CSMs, client management, etc.
- Introduce new event types, decide where they want them logged, how frequently these should be reported and who should be alerted.
- Set up reports to review different activities, from monthly summaries of jobs completed, to the number of logins by user, as well as filtering data, location stats, etc.
- Send and receive messages with attachments.
A window on security
LIMIT allows clients to exchange information with Profile in real time, so everyone is always up to date. From details of events as they unfold to seeing the big picture in terms of performance, spending and a host of other parameters.
For a personal illustration of how LIMIT could keep you in touch, contact Profile’s Technical Director, Chris McKay, on 01469 533 339.